This will be my final required post for this blog. But before I take my hiatus, we’re going to, as the title states, go back to the basics of what this venue has been all about: rhetoric, digital culture, and the meaning of our language/actions in our real and online lives.
So below are some bonus topics that relate to the end of the course, a topic of recent posting history, and one all time favorite topic (oversharing and social media fails) that I’ve been writing about throughout this blog, all the way back to the very beginning.
So let’s start with the present:
1. My Course Project: Hootsuite and Effective Twitter Engagement
Throughout the Social Media for PR course, I’ve been working on a project in which I’ve had to become certified via HootSuite University. Hootsuite offers three kinds of professional certifications, and of these, I’m participated in the Higher Education course. It uses mostly videos and other online training materials
You can view a sample of the training material here. The videos, however, encompass the vast majority of the “lecture” equivalent of the course. As far as project execution, that’s all learned by doing on one’s own HootSuite Dashboard. For those unfamiliar, here’s a quick peek at mine:
2. Online Security: Twitter, 3rd Party Apps, and the Internet-at-large Edition
This blog has already covered security in social media generally and on Facebook (and to a lesser degree Tumblr) specifically farely extensively, as well as the damning consequences of oversharing.
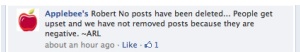
Completing the HootSuite project has caused my to violate my own rule of thumb regarding third-party apps that share info between platforms, which is–in brief–don’t use them. From the very moment I added my Facebook feed (a requirement of the project), I got this lovely little message asking for permission to manage my personal and professional pages (for me, that includes my admin status on two record labels and my two bands**), and much, much more:

Several more like it appeared in subsequent screens, and all of them sent my personal online security alarms blaring. I elected to “skip” those that offered the option, but ultimately had to allow some info to be shared for the feed on HootSuite to have any functionality whatsoever.
And this, friends, is the tradeoff we make by choosing to use the internet at all. For every service we use, including (arguably especially) Google, we offer bits of our data and bits of our private lives, all of which can be linked back to us by anyone with a bit of time to do the legwork and a minimal amount of technical know-how. Want to use Siri on your iPhone? Well, don’t be surprised that everything you asked her is banked in a data vault owned by Apple and, yes, traceable to you. Regarding Google, they have a vault that stores all of your search queries for 18 months. In class, we watched one great documentary called Inside the Mind of Google with loads more on this subject and its surprising consequences, viewable here.
3. Social Media Fails: in the News
All of this heavy security talk is giving me a hankering for something light. So let’s go over some of the better social media fails in recent news that I haven’t already discussed here.
Here are just a few highlights (in a style not at ALL reminiscent of NPR’s “Wait Wait…Don’t Tell Me!”):
- Kanye West’s managers allowing him to tweet…anything. Ever. This caustic, vulnerable rapper is either the worst candidate for social media or the reason it was invented in the first place.
- Anthony Weiner Craigslisting and publishing partially nude photos of himself, then announcing his return to politics…On (where else?) Twitter.
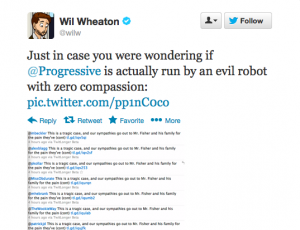
- Pretty much everything on…This infographic.
Virtually all of these misfortunes could have been avoided with better security or better safeguarding of one’s information and identity (real or online).
Bringing It All Back Home
So yes, the three above topics–the two old (security, SM fails), and one new (#1, Hootsuite)–are indeed all related, not just to each other, nor just to my interests, but to the origin and focus of this blog. And moreover, they relate to all of us who choose to participate in digital culture. We’ve already opted in to the security risk of using social media. Even those who haven’t, have opted into the risk of being a part of digital culture by using a SmartPhone with a data plan. You opted in by accessing this blog, whether you found it as a user of WordPress, Google, Bing, another search engine, or even another blog.
So is having an online presence worth the risk? Only you can decide. As for me, I believe we increasingly need these tools to participate in a digital culture that is increasingly integrated with real-world culture, from the local level all the way up to the global. But just be wise in what you put out there, and be aware that once you’ve presented data, you have (in most cases) entrusted it to someone else: a cookie-based ad service, social media network, a corporation, or sometimes, a cloud.
So my hiatus begins. So long for now, and be careful out there, fellow digital culture warriors!
_ _ _
**For those interested in my music and other good music, please take a look at Red Mynx Records, my current label for me and other interesting and unique artists. You can hear a free preview of one of my songs with my duo Iolite here. Written and recorded by the two of us in a 20 minute four-track session. If you like indiepop, The Smiths, or Depeche Mode, you’ll like this.